Re-Installing Self Sign Certificate in Exchange 2007
The default self-sign certificate that comes with the Exchange 2007 was deleted after installing a new certificate from Verisign. But as luck would have it, the name of our company got changed and for compliance purpose, we had to change the certificate so that the new company name is projected. It took almost two weeks for the new certificate to come. But in the meantime we had to use a certificate (a self-sign one at the least) as Exchange 2007 cannot run without a certificate we had already deleted the self sign cert that comes by default. The steps below will tell you the ways that I have taken to fix it.
After many trial and errors, the self-sign certificate is working now. I cannot guarantee that information given below will perfectly work for you. {Continue at your own risk}
- Open Exchange Management Shell (EMS) and type the command as shown below to generate the Certificate Signing Request (CSR)
A thumbprint (something like) 6B8F25E721DDFC2C552934BE2FB8F2207D0E5FA8 will be generated.
New-ExchangeCertificate is fed with the GenerateRequest parameter showing that here we are not truly creating a new Certificate but just a request. The resulting request will be saved to disk at the specified path base64 encoded. The SubjectName and DomainName are the parameters identifying the Certificate Subject and Subject Alternative Name extension respectively. Running the command will generate the request at the specified path.
- The request has to be handed to a Certification Authority like Verisign, Comodo, etc. for processing. In this scenario, I will make a server act as a Certification Authority (CA). Steps to configure the CA are as follows:
Get a server and install the "Certificate Authority" from the Add Remove Programs (Windows Components). Make sure that the server is a member server of that domain (or else, it acts funny by being very slow on accessing the site).
Submit the new request as shown in the image below. If the GUI version throws an error, then use the command line "CERTREQ.EXE" to submit the request. After this, we can use the the remaining steps through the GUI.


- Once the request is uploaded, export the certificate as shown below:
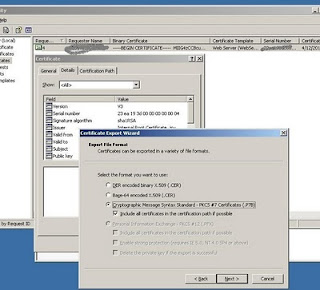 Transfer the exported file to a location in the Exchange Server. In the Exchange Server, we need to import the new certificate. The step is given below.
Transfer the exported file to a location in the Exchange Server. In the Exchange Server, we need to import the new certificate. The step is given below.
Exchange will now install the new Certificate. In the Certificates list returned by Get-ExchangeCertificate, this will replace the entry that was created on running New-ExchangeCertificate to generate the request.
- We then enable the new certificatye for the services and remove the old certificate. The steps are given below.
Confirm
Overwrite existing default SMTP certificate, '7B0BA23F33FDFCDB876CA47FC8EE3E0AFB109385' (expires 4/11/2012 1:38:23 PM), with certificate
'E6CFAE71BAC4405D1B4B4C47EB2DCE4668243D30' (expires 4/11/2012 2:29:13 PM)?
[Y] Yes [A] Yes to All [N] No [L] No to All [S] Suspend [?] Help (default is "Y"): y
- Next using the cmdlet that follows, we assign the new Certificate all the services for this Exchange server:
[PS] C:\Documents and Settings\Administrator>Remove-ExchangeCertificate -Thumbprint 7B0BA23F33FDFCDB876CA47FC8EE3E0AFB109385
Confirm
Are you sure you want to perform this action?
Remove certificate with thumbprint 7B0BA23F33FDFCDB876CA47FC8EE3E0AFB109385?
[Y] Yes [A] Yes to All [N] No [L] No to All [S] Suspend [?] Help (default is "Y"): y
Remove-ExchangeCertificate -Thumbprint C52A264821E83E92173D5E44DC3DDEE0F8CBEB2F
- After all this has been set, deploy the certificate through Group Policy

Comments
Post a Comment